The 2026 Enterprise CCaaS Strategic Evaluation

A definitive analysis of the enterprise CCaaS landscape in 2026, comparing Genesys, NICE, and AWS for global decision makers.
Read more →
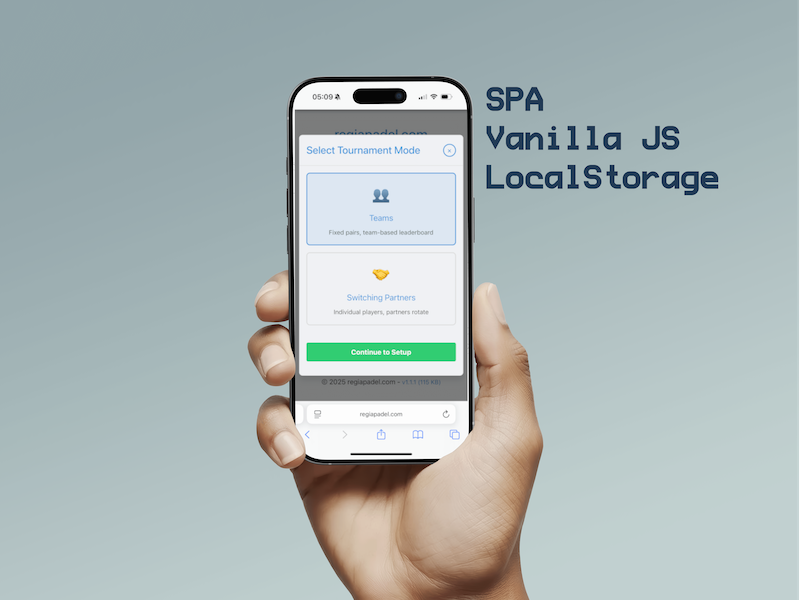
How I Built RegiaPadel.com: A Lightweight Americano Padel Tournament Manager

Learn how I created RegiaPadel.com, an ultra-light Americano padel tournament manager built from scratch with vanilla JavaScript, and no frameworks. My journey to scratch my own itch and deliver a practical, blazing-fast app for players and organizers.
Read more →
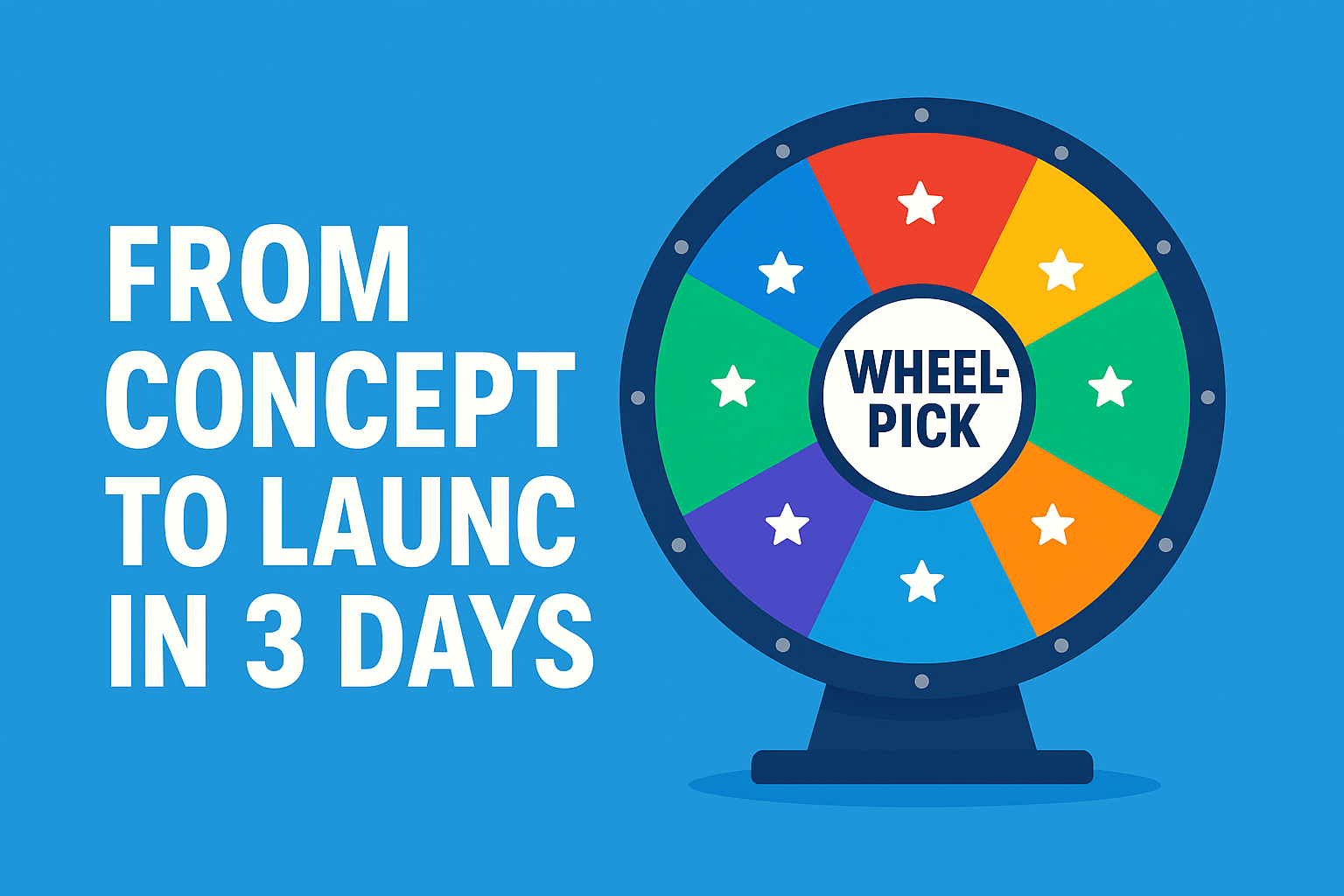
Building Wheel-Pick.com: From Concept to Launch in 3 Days

Discover the journey of creating wheel-pick.com, a free online wheel spinner for random decisions. Learn about the technical challenges, design decisions, and lessons learned throughout the development process.
Read more →
Console Wars: A Battle of Specs or Just Tribal Loyalty?

For decades, gamers have waged war over which console reigns supreme. But is it really about specs and exclusives—or just brand loyalty in disguise?
Read more →

Tracing Nvidia’s Journey with Open Source: Milestones, Challenges, and What’s Next

Explore Nvidia’s history with open source, diving into its milestones, challenges, and future direction in the evolving tech landscape.
Read more →
How to Compress Folders in FreeBSD Using Find and Tar

Learn how to compress directories in FreeBSD using a simple find and tar command for efficient file management.
Read more →

Enhance Your Ethical Hacking Skills with HackingLab: The Best Open-Source Practice Environment

Explore HackingLab, the best open-source platform for practicing ethical hacking and penetration testing techniques.
Read more →

Is Your Personal Data at Risk? Protect Yourself by Removing It from 570+ Sites with Optery

Discover how exposed personal information online can put you at risk and how Optery can help you remove it from over 570 sites.
Read more →

How to Send a SWIFT Wire From Scratch

Learn how to send a SWIFT wire transfer from scratch. This guide covers the basics of SWIFT, step-by-step instructions, and key considerations for global transactions.
Read more →

Boost Your Data Analytics Workflow with Pingouin: A Powerful Python Statistical Package

Learn how to boost your data analytics workflow with Pingouin, a powerful Python statistical package. Explore its benefits, code examples, and performance improvements over traditional libraries like NumPy and Pandas.